[ad_1]

Hackers for considered one of Russia’s most elite and brazen spy companies have contaminated dwelling and small-office community units around the globe with a beforehand unseen malware that turns the units into assault platforms that may steal confidential information and goal different networks.
Cyclops Blink, because the superior malware has been dubbed, has contaminated about 1 p.c of community firewall units made by community machine producer WatchGuard, the corporate said on Wednesday. The malware is ready to abuse a reliable firmware replace mechanism present in contaminated units in a method that offers it persistence, which means the malware survives reboots.
Like VPNFilter, however stealthier
Cyclops Blink has been circulating for nearly three years and replaces VPNFilter, the malware that in 2018 researchers discovered infecting about 500,000 dwelling and small workplace routers. VPNFilter contained a veritable Swiss Military knife that allowed hackers to steal or manipulate site visitors and to watch some SCADA protocols utilized by industrial management techniques. The US Division of Justice linked the hacks to the Major Intelligence Directorate of the Normal Workers of the Armed Forces of the Russian Federation, usually abbreviated because the GRU.
With VPNFilter uncovered, Sandworm hackers constructed a brand new malware for infecting community units. Like its predecessor, Cyclops Blink has all the trimmings of professionally developed firmware, nevertheless it additionally has new tips that make it stealthier and tougher to take away.
“The malware itself is refined and modular with fundamental core performance to beacon machine data again to a server and allow recordsdata to be downloaded and executed,” officers with the UK’s Nationwide Cyber Safety Heart wrote in an advisory. “There may be additionally performance so as to add new modules whereas the malware is operating, which permits Sandworm to implement further functionality as required.”
Holding the WatchGuard hostage
To date, the advisory acknowledged, Sandworm has “primarily” used the malware to contaminate community units from WatchGuard, however the hackers are possible in a position to compile it to run on different platforms as effectively. The malware beneficial properties persistence on WatchGuard units by abusing the reliable course of the units use to obtain firmware updates.
The malware begins by copying firmware pictures saved on the machine and modifying them to incorporate malicious performance. Cyclops Blink then manipulates an HMAC worth used to cryptographically show the picture is reliable so units will run it. The method appears like this:
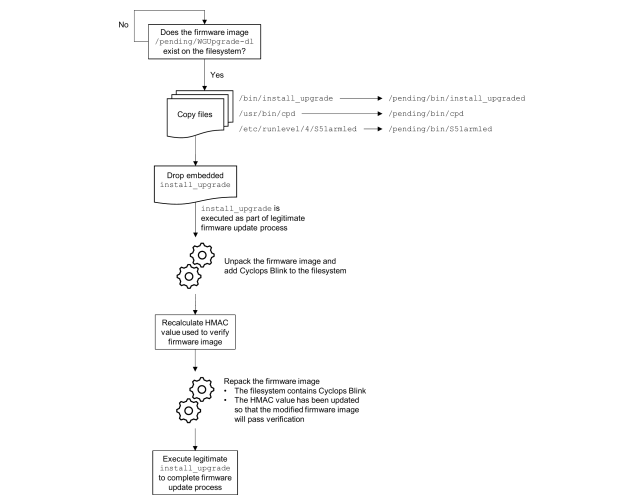
The malware accommodates a hard-coded RSA public key, which is used for C2 communications, in addition to a hard-coded RSA personal key and X.509 certificates. However they don’t seem like actively used inside the samples analyzed by the UK officers, making it doable that they’re meant for use by a separate module.
Cyclops Blink makes use of the OpenSSL cryptography library to encrypt communications beneath encryption supplied by TLS.
Wednesday’s advisory acknowledged:
Every time the malware beacons it randomly selects a vacation spot from the present record of C2 server IPv4 addresses and hard-coded record of C2 ports. Beacons encompass queued messages containing information from operating modules. Every message is individually encrypted utilizing AES-256-CBC. The OpenSSL_EVP_SealInit perform is used to randomly generate the encryption key and IV for every message, after which encrypt them utilizing the hard-coded RSA public key. The OpenSSL_RSA_public_decrypt perform is used to decrypt tasking, acquired in response to beacons, utilizing the hard-coded RSA public key.
Different new measures for stealth embrace use of the Tor privateness community to hide the IP addresses utilized by the malware. UK officers wrote:
Sufferer units are organised into clusters and every deployment of Cyclops Blink has an inventory of command and management (C2) IP addresses and ports that it makes use of (T1008). All of the recognized C2 IP addresses thus far have been utilized by compromised WatchGuard firewall units. Communications between Cyclops Blink purchasers and servers are protected beneath Transport Layer Safety (TLS) (T1071.001), utilizing individually generated keys and certificates. Sandworm manages Cyclops Blink by connecting to the C2 layer by the Tor community:

